What should be in your tech security stack? This is the question businesses are asking themselves wi...

Lorem ipsum dolor sit amet, consectetur adipiscing elit.

What should be in your tech security stack? This is the question businesses are asking themselves wi...
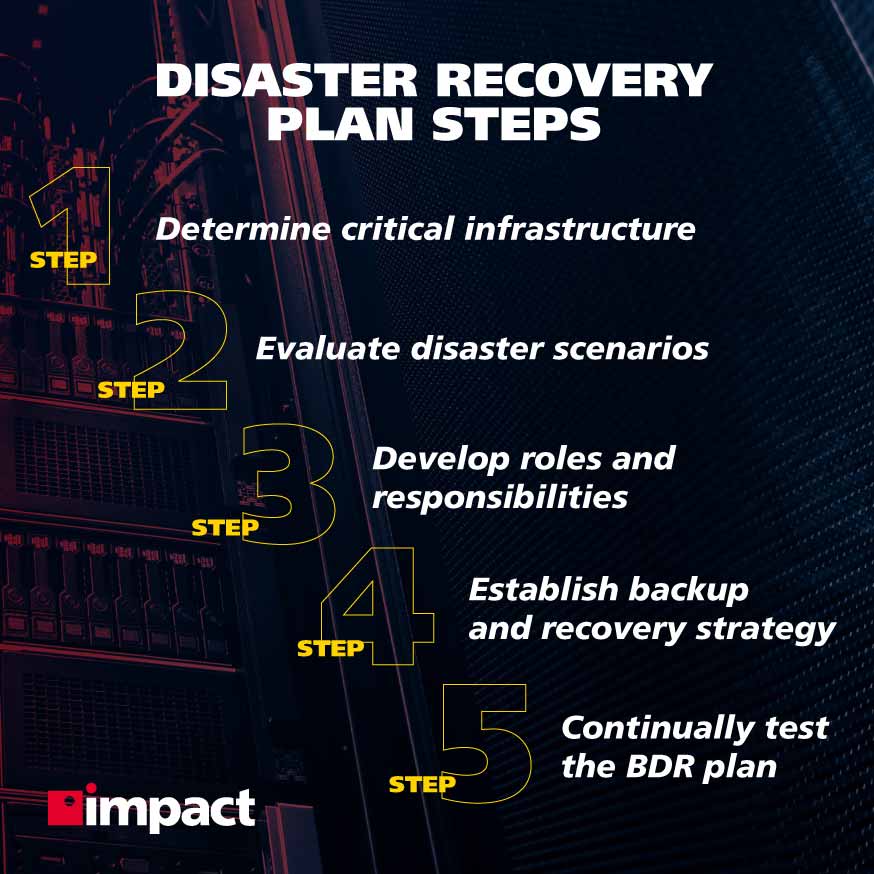
Take a look at these disaster recovery steps to get a clear understanding of what a business should ...

What Is a Site-to-Site VPN Technology? Site-to-site VPN is a type of VPN that keeps data encrypted b...

Cyberattacks have been on the rise for a number of years, with the pandemic bringing a sharp rise in...

If you’re looking to secure your work network, you may have heard of DNS layer security. DNS layer s...
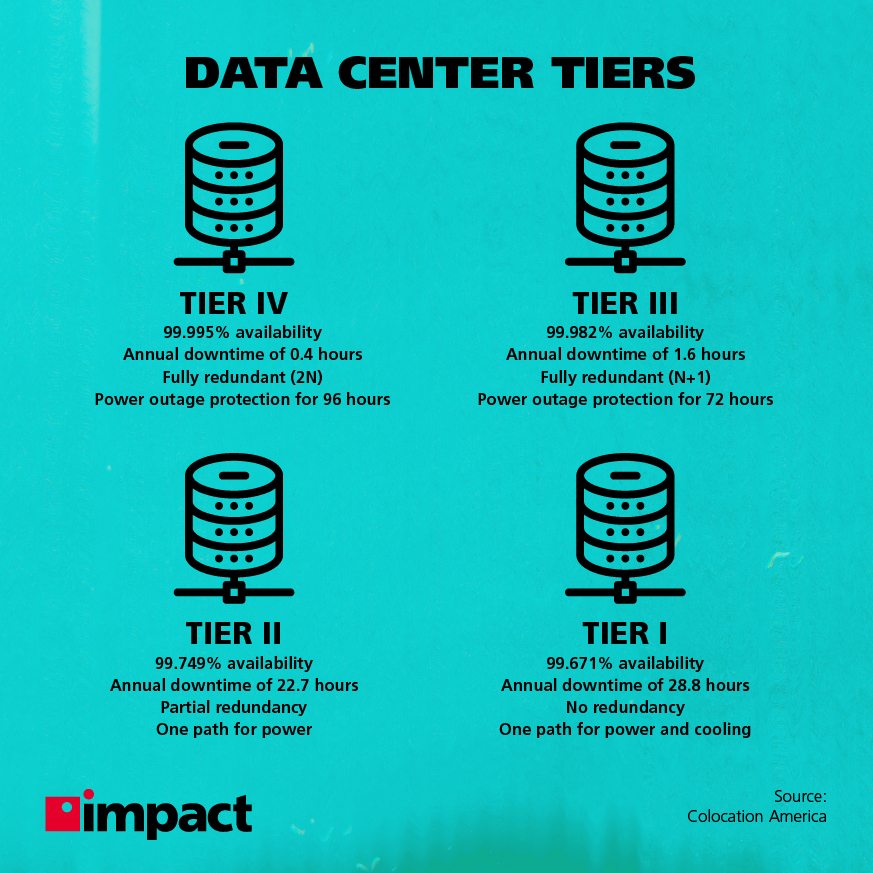
Data Center Tiers Explained Data center tiers are established rankings for the performance of server...

What is next-gen antivirus? (definition): Next-gen antivirus uses a combination of modern technology...
What Does CCPA Stand For? CCPA stands for the California Consumer Privacy Act (CCPA), a digital cons...

What Does HIPAA Mean? What is HIPAA exactly and what do you as a company need to do to stay on the r...

Welcome back to our series, Cybersecurity Monthly, where we’ll be presenting you a round-up of updat...
Lorem ipsum dolor sit amet, consectetur adipiscing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua.